General description
Type: BackDoor Malware
Malware names:
Backdoor.Win32.SunBurst
BackDoor.SiggenNET
Trojan.MSIL / Solorigate
Degree of destruction: average
Prevalence: average
What is Backdoor Malware?
Backdoor malware is a program that allows hackers to bypass the system’s security mechanism and provide various sources of that system to hackers. Hackers can use this method to enter the system without authentication and do not have to worry about changing the username and password. Backdoor malware comes in many forms that hackers use for their purposes of intruding on a system’s resources.
What is SolarWinds tool backdoor infection?
On December 20, 1999, SolarWinds Co. that is the manufacturer of software products announced that it was the victim of a cyber attack as a result of which the software versions SolarWinds Orion that were published between March 1998, and August 1999, contained a backdoor code. This backdoor allows hackers to execute any command type remotely on the system and thus the victim network if the software is connected to the Internet.
Estimates show that at least 18,000 of the company’s official customers have installed infected versions and are at risk. The security company FireEye, Many US government and security agencies, and at least seven other countries were among the victims.
Infected SolarWinds Orion versions are as follows:
– 2019.4 HF 5
– 2020.2
– 2020.2 HF 1
If any of the SolarWinds Orion versions you have installed or have installed the mentioned one, you need to carefully check the network for infection or intrusion.
The high degree of danger of this backdoor, the possibility of complete remote control over the victim system, the access of the system that Orion is installed on all critical equipment and servers of the network, as well as the degree of skill and sophistication of the intruders who have used this backdoor, complicates dealing with this issue and examining it, and it is recommended that you use the help of expert forensic teams.
Additional information
The scenario used in this attack is that the intruders have used a supply chain attack to achieve their goals. In supply chain attacks, the intruder detects the devices used in its target network without direct penetration into the main target systems and aims at these devices. This type of attack can be very risky, as software and equipment purchased from trusted sources are often not carefully reviewed.
About software, SolarWinds Orion is used in many large and small networks around the world, and attackers target such software due to its nature (Which is a network management system (NMS)) that will be installed in the center of the network and has direct access to all network equipment and servers.
As a result, by infecting the SolarWinds Orion, all that the hackers needed to do was wait for the victims to install the software. The software backdoor is activated after 12 to 14 days after installing the vulnerable version, and it communicates with its Command and Control server to receive commands. Having the full name and profile of the infected system, the intruder will simply select its victim and proceed with the rest of the intrusion process.
Note that all infected versions of this malware that have been released in the relevant period have a SolarWinds digital signature.
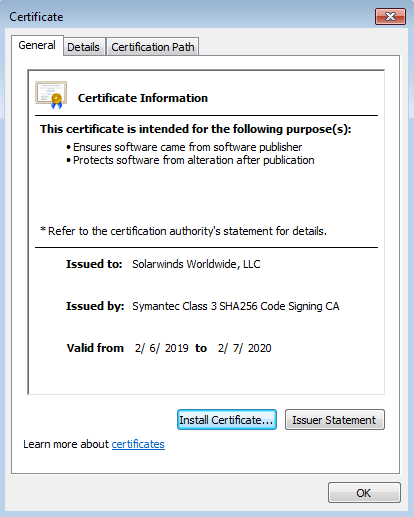
Figure 1- Solarwinds Digital signature certificate
Infection profile
1-Update Orion tools between March 98 and December 99 (This alone is characteristic of system infection and requires a forensic examination)
2- View the connection to any of the following addresses:
• avsvmcloud.com
• digitalcollege.org
• freescanonline.com
• deftsecurity.com
• thedoccloud.com
•etc
3- See the connection with each following IP:
• 13.59.205.66
• 54.193.127.66
• 54.215.192.52
• 34,203,203.23
• 139.99.115.204
•etc
How to deal with it and disinfect the system
If you have performed an update for each SolarWinds product in the mentioned period (March 1998 to December 2010), your network (Not just the system on which the tool is installed) Is intrusive, and deleting or updating software does not secure your network. In this regard, it is necessary to find and neutralize all possible infections and ways of intrusion, with the help of relevant experts and complete the network forensics. Also, you need to put the following actions on your agenda:
1- Create a Snapshot from the previous status of all system files which somehow connected to SolarWinds products and connect an expert forensic team.
2- Disconnect network management and monitoring software from the Internet and put it on a separate VLAN that is not accessible from the Internet (What if you use any other product SolarWinds products)
3- Isolating networks of affected systems
4- Change all passwords used at the network level (This should be done after isolation and not communicate with the new systems in any way with the new identity information.).
5- Update the infected versions to the version presented on December 16, 2016 (December 15, 2020) From this address
* If you also use other products of SolarWinds except for Orion, it is better to check all the connections of the relevant systems and update the latest version provided by reputable sites as soon as possible.
Padvish Antivirus Identifies the Infected versions of this tool that are called Backdoor.Win32.SunBurst and Padvish IPS also prevents communication with the known malware C&C servers.
In addition, Padvish Forensic Analysis Team is ready to respond to the general users and organizations that need to investigate Forensics in their network.