- ID: CVE-2021-44228
-
Score: 10 (Of 10)
-
CVSS: Critical
-
Type of vulnerability: Remote Code Execution
-
Error type: Code injection
Additional information
A critical vulnerability (CVE-2021-44228) in the popular open-source library Apache Log4j threatens thousands of third-party applications and services that use this library. Published code to exploit a vulnerability indicates an attacker can use RCE (Remote Code Execution) vulnerability and abuse a registered specific string through Log4j. An attacker can then execute arbitrary code from an external source. The Apache Software Foundation recently published an emergency patch for this vulnerability. Affected organizations have to update to Log4j 2.17.0 as soon as possible or, if an upgrade is not possible, put the mentioned countermeasures on their agenda.
Vulnerable versions
-
All versions Apache Log4j From 2.0-beta9 until the 2.14.1
-
All software from Log4j Vulnerable uses a range of VMware، Solr and even includes enterprise and custom software.
How to deal with this vulnerability
You can use one of the following ways to deal with this vulnerability:
-
Update to version 2.17.0 Log4j (link)
-
Only for versions 2.10 and above: there’s an added configuration for disabling the corresponding capabilities in these versions, and you can use one of the following methods:
-
Insert “setting
log4j2.formatMsgNoLookups = true” in the right place in the software configuration (It varies depending on the software) -
Run the Java program by adding a command-line
"Dlog4j2.formatMsgNoLookups = true" -
Setting the environmental variable
"LOG4J_FORMAT_MSG_NO_LOOKUPS = true"-
Change file
/ etc / environment -
in the Linux operating system.
-
Use Edit System Environment UI in the Windows operating system.
-
-
-
Only for versions 2.0 to 2.10.0: Delete JndiLookup class from the log4j-core class route, which you can execute a command similar to the following command:
zip -q -d log4j-core - * .jar org / apache / logging / log4j / core / lookup / JndiLookup.class
Note that, in all cases, you have to restart the vulnerable program to receive the configuration. (Reset the system for environmental variables)
How do I find vulnerable systems on the network?
Unlike most vulnerabilities, which are limited to specific software, one of the main vulnerabilities is that Log4j exists in a wide variety of different software and even custom and specifically made software that you need to search the whole network to find them.
Because many of your Java-based software and systems may have a compiled vulnerable file, updating the software package is not enough, and you should search all the compiled software for the vulnerable module.
Use one of the following commands to find all vulnerable software, depending on the operating system. Note that these commands only use the module log4j, and even updated versions are reported.
Find vulnerable software in the Linux operating system
Be sure to follow the instructions with the user root Run to scan the entire system.
find / -type f -name '*.?ar '-print0 | xargs -0 fgrep JndiLookup.class
find / -type f -name '* .class' | fgrep JndiLookup.class
If the output is seen, the path of the vulnerable software is displayed
Find vulnerable software in the Windows operating system
The following commands in Each drive Run separately.
Be sure to follow the instructions with the user root Run to scan the entire system.
dir / s / b \ *. jar \ *. ear \ *. war | findstr / f: / / m JndiLookup.class
dir / s / b JndiLookup.class
If the output is seen, the path of the vulnerable software is displayed
Scanning of vulnerable systems by antivirus
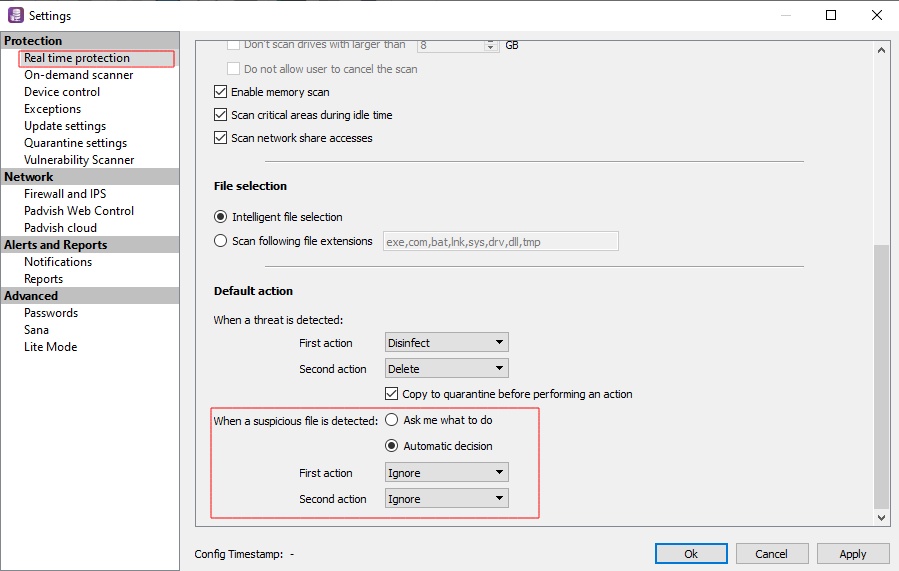
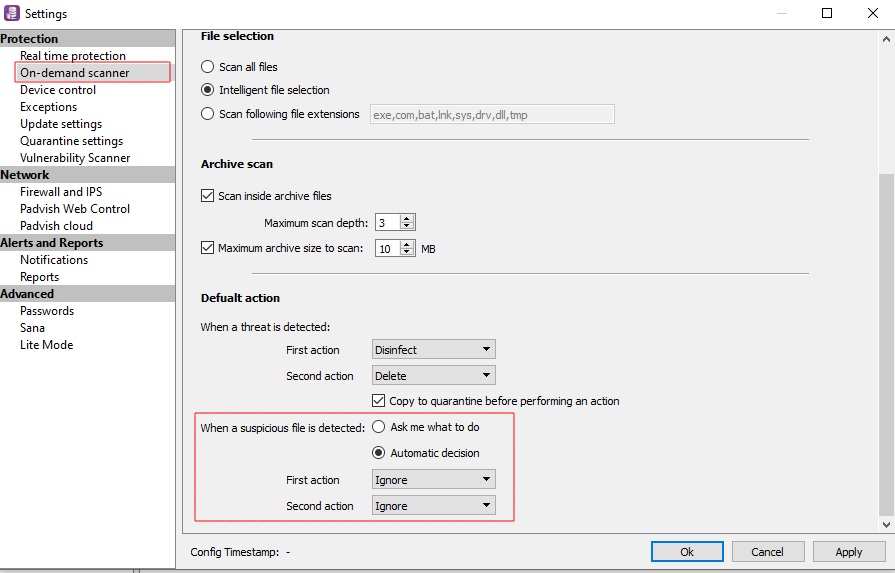
Padvish Antivirus console users can use the following method to search for vulnerable software in their organization.
For this purpose, it is necessary to have a special signature database to identify vulnerabilities log4j Download and scan your systems. Any software that has used this library will be reported to you as “PUA.JAVA.PotentiallyVulnerable.Log4j“.
For this purpose, it is recommended to perform the following steps:
-
Vulnerability identification signature database log4j Download from the link below and enter inside the console.
-
Make sure all systems have received the update by referring to Managed Computer. (If needed from Force Update Use)
-
Temporarily change the antivirus settings to ignore the suspicious diagnoses. It is recommended to make this change so as not to block access if vulnerable software is found.
-
Then run the Full scan task on your desired systems.
-
Finally, after ensuring that the scan is complete, Reset all settings.
Requirements in the Padvish consol