Overview
- Vulnerability Type: Remote Code Execution (RCE)
- Danger Level: Critical (CVSSv3: 9.8)
- Vulnerable Platform: Microsoft Windows
- Security Patch Submission Date: 12 June 2024
- Vulnerable Versions: All versions of Windows Server, Windows 10, and Windows 11
- Usage Status: Proof of Concept (PoC)
Technical Description
A critical flaw in Microsoft Message Queuing (MSMQ) was fixed in Microsoft’s June 11th, 2024 patch. MSMQ is a messaging protocol that facilitates communication between applications across different networks and systems, even when they are temporarily offline. Applications send and read messages to and from a queue. Identified as CVE-2024-30080, this vulnerability is a use-after-free flaw exploitable by unauthenticated attackers sending a malicious MSMQ packet to port 1801. Successful exploitation allows remote code execution (RCE) on servers or clients running MSMQ, enabling attackers to take control of the affected systems.
This vulnerability has a CVSS score of 9.8, categorizing it as critical. Full details of the vulnerability have not been disclosed to prevent further exploitation.
According to Microsoft, the CVE-2024-30080 flaw allows an unauthenticated remote attacker to execute arbitrary code on the target system and gain system access by sending a specially crafted message to the MSMQ service. This can enable intruders to install applications, view, modify, or delete data, create new accounts with full access, and ultimately take control of the system.
Vulnerable Versions
The CVE-2024-30080 vulnerability affects the MSMQ service in general and all versions of Windows 10, Windows Server, and Windows 11.
Indicators of a vulnerable system include:
- MSMQ HTTP-Support feature enabled
- A running service called Message Queuing
Exploit
How to patch the vulnerability
Microsoft has released security updates to fix this vulnerability. All users are strongly advised to apply Microsoft’s June security patches immediately.
Mitigation Measures
?Padvish users should restrict access to port 1801 using the Padvish Antivirus firewall component.
? The activation of the Windows MSMQ service makes a system vulnerable to this exploit. This feature can be managed through the Control Panel.
To diagnose vulnerability, check if the MSMQ HTTP-Support feature is enabled and if the Message Queuing service is running on the device.
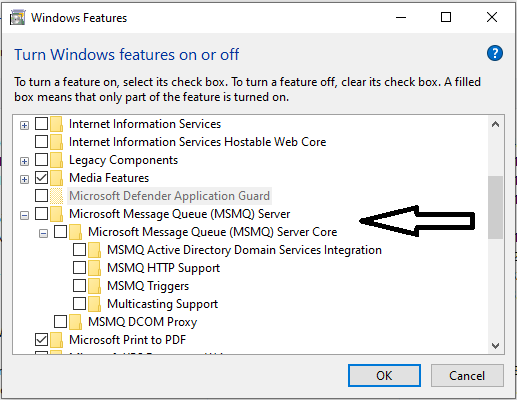
? Enabling or disabling the MSMQ option is done through the following path:
Control Panel ➡️ Programs ➡️ Programs and Features ➡️ turn windows features on or off ➡️ Microsoft Message Queue (MSMQ) server
Recommended Actions to Reduce Exploit Severity:
✅Limit the MSMQ service to trusted networks only.
✅Enable firewalls to restrict access to ports associated with MSMQ service