Introducing the exploit
CVE-2022–41040 Vulnerability Score: 6.3
Vulnerability Type: SSRF
CVE-2022–41082 Vulnerability Score: 8.8
Vulnerability type: RCE
Vulnerable platform: Windows Server 2012, 2016, and 2019
Date of last security patch provided: 08-11-2022
Introduction
The generality of this vulnerability is similar to the proxyshell vulnerability for 2021 and includes the following 3 cves:
CVE-2021-34473 (KB5001779) •
CVE-2021-34523 (KB5001779) •
CVE-2021-31207 (KB5003435) •
With the difference that there is a need for authentication in vulnerability 2022, it should be said that attackers use two vulnerabilities 41040 and 41082 in order to create a webshell in the victim’s system.
How to identify the possibility of vulnerability
Since the general trend of the said vulnerability is similar to its 2021 version, when examining the evidence, the following can be suspicious:
- There is a process named “*\w3wp.exe” that contains the following commands:
[“*&ipconfig&echo*”, “*&quser&echo*”, “*&whoami&echo*”, “*&c:&echo*”, “*&cd&echo*”, “*&dir&echo*”, “*&echo [E]*”, “* &echo [S]*”]
- Existence of suspicious subprocesses in [“*\WerFault.exe”, “*\csc.exe”] with parent process w3wp.exe
- In some of the observed attacks, attackers use certutil tool to download webshells, so the presence of “*\certutil.exe” process, which includes commands such as [“* -urlcache *”, “* /urlcache *”] should be investigated. take
- Creating suspicious files with event id = 11 in the usual paths that attackers use to download payloads:
[“C:\Users\Public*”, “C:\PerfLogs*”, “C:\root*”]
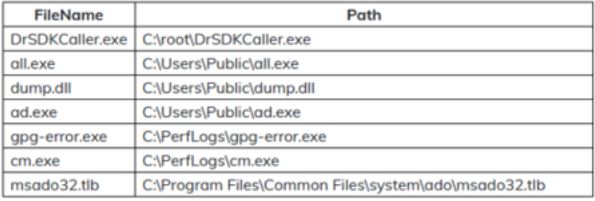
Screenshot from 2022-12-24 11-42-58.png
- Existence of logs like the following log in iis:
autodiscover/autodiscover.json?@evil.com/<Exchange-backend
endpoint>&Email=autodiscover/autodiscover.json%3f@evil.com
- The presence of webshells with often obscured content in paths such as the following table:
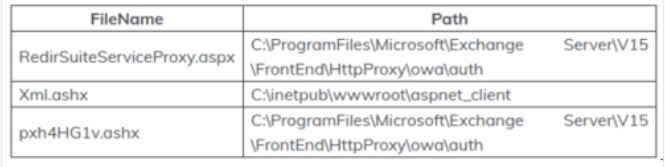
Screenshot from 2022-12-24 11-41-54.png
- The existence of dll or suspicious files in the following address:
C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy
- In directories such as those mentioned:
/ews/web/webconfig/
/owa/auth/webcccsd/
/ews/auto/
/ews/web/api/
/owa/auth/Current/script/
Necessary security considerations to reduce the possibility of an attack
The best solution to protect users from this vulnerability is to install the updates provided by Microsoft from the following link:
https://techcommunity.microsoft.com/t5/exchange-team-blog/released-november-2022-exchange-server-security-updates/ba-p/3669045
∗ If it is not possible to install updates, the alternative solutions are as follows:
- URL Rewrite rule mitigation
- Disable remote user access to the powershell process
In this case, it is recommended that Exchange Server users implement both the URL Rewrite rule mitigation provided for CVE-2022-41040 and PowerShell remote control access to reduce the possibility of intrusion (CVE-2022-41082) by people who are admins. They cannot disable it.
For URL Rewrite rule mitigation, Microsoft has provided 3 solutions to users, depending on the conditions and type of policies of the organization, it is necessary to use one of the 3 cases to apply the rules in the URL Rewrite configuration:
- The first solution:
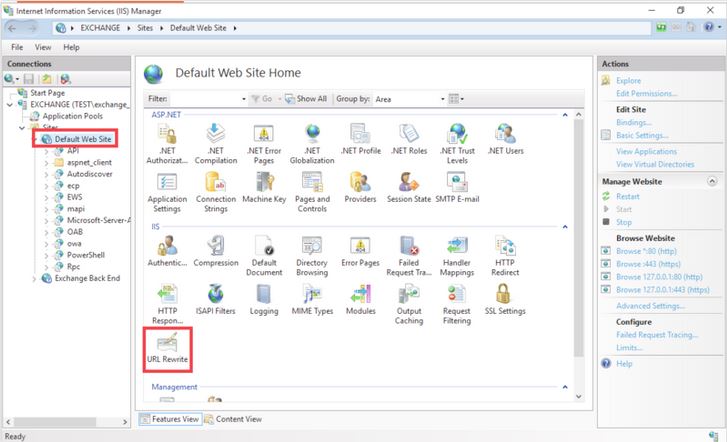
Proceed as follows by referring to the iis settings:
¤ Select Default WebSite
¤ Select URL Rewrite from the displayed window:
¤ From the right side of the action section, select Add Rule(s):
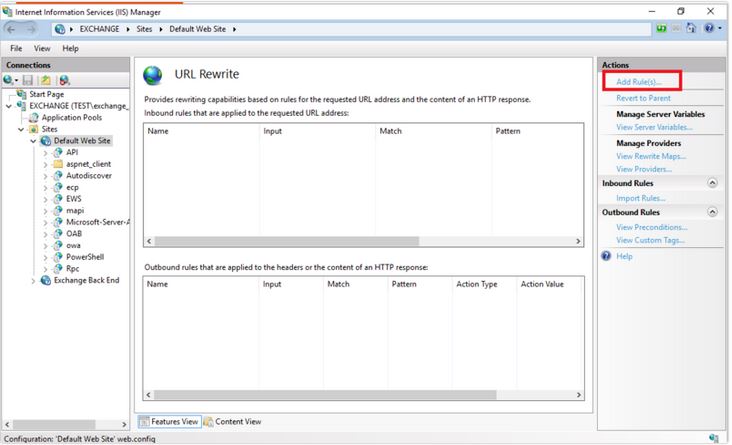
¤ Select Request Blocking and click on the ok option:
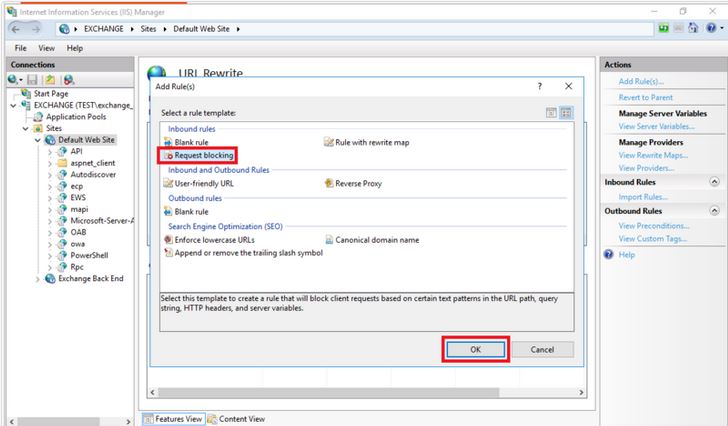
¤ Add the following string in the blocked requests section:
“(?=.*autodiscover)(?=.*powershell)”
¤ Choose Regular Expression from the Using section.
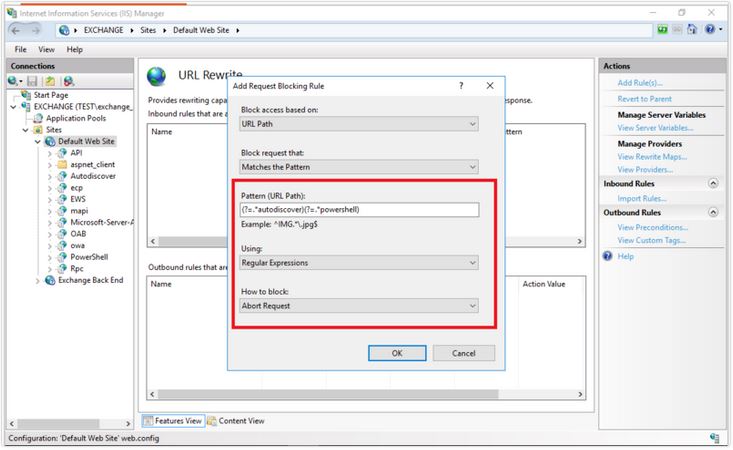
¤ Select the Abort Request option from the how to block section and the ok option.
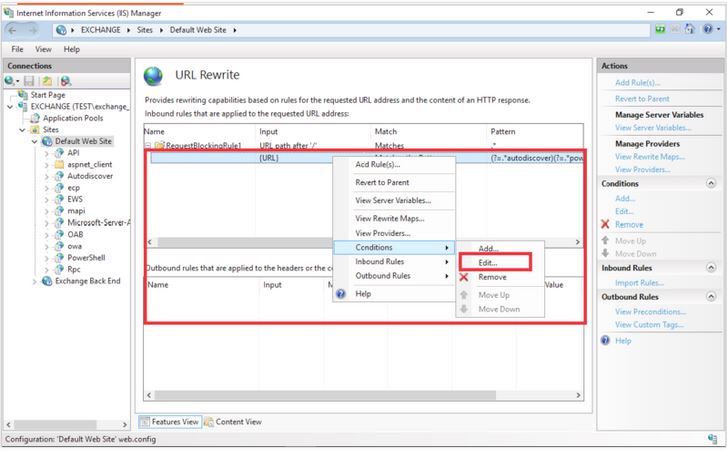
¤ By selecting the created rule and selecting edit from the conditions section:
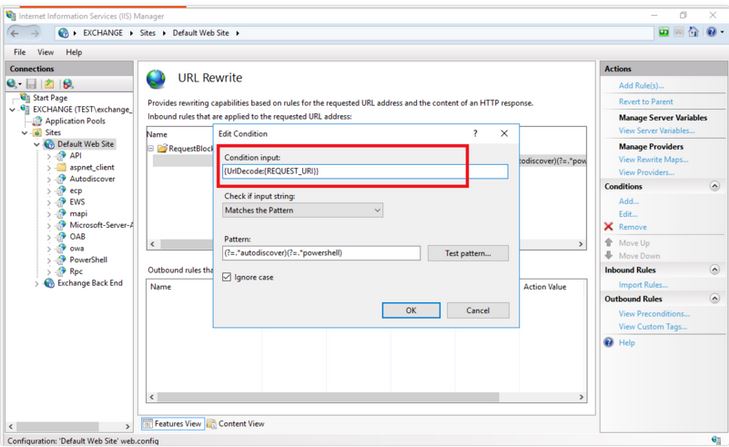
¤ Change the input condition from {URL} to {UrlDecode:{REQUEST_URI}}:
- The second solution:
Using the EOMTv2 script provided in the link below will automatically apply the changes mentioned in the previous section.
Script link
ttps://aka.ms/EOMTv2
- The third solution:
For users whose Exchange Emergency Mitigation Service (EEMS) is active, the procedure mentioned in the first solution is done automatically and no action is required from the user.
How to patch the vulnerability
Link to updates provided for CVE-2022–41040 and CVE-2022–41082:
Exchange Server 2013 CU23 ♦
Exchange Server 2016 CU22 and CU23 ♦
2Exchange Server 2019 CU11 and CU12 ♦
References:
https://techcommunity.microsoft.com/t5/exchange-team-blog/released-november-2022-exchange-server-security-updates/ba-p/3669045
https://www.logpoint.com/en/blog/proxynotshell-detecting-exploitation-of-zero-day-exchange-server-vulnerabilities/
https://msrc-blog.microsoft.com/2022/09/29/customer-guidance-for-reported-zero-day-vulnerabilities-in-microsoft-exchange-server/
https://www.gteltsc.vn/blog/warning-new-attack-campaign-utilized-a-new-0day-rce-vulnerability-on-microsoft-exchange-server-12715.html