Introduction
Introducing WPAD
Web Proxy Auto-Discovery or WPAD provides organizations with a way to automatically configure a proxy server on the system; This feature means that you don’t need to set it manually in the organization.
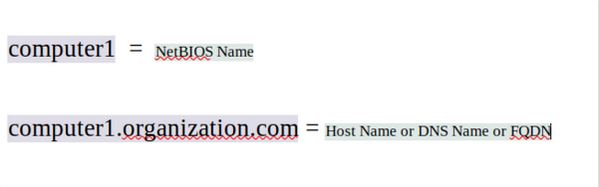
Introduction of NetBIOS and NetBIOS Name
NetBIOS is a program that enables the communication between different computers within a local area network (LAN).
NetBIOS Name = The names of the computers seen in the network are their NetBIOS Names, which are published by the Broadcast mechanism in the network and are visible to others. Every time the computer is turned on or off or restarted, every time this operation is performed, the Broadcasting process is performed. It is possible that this issue is not acceptable in large networks.
In corporate networks, although services such as WINS can be used to centralize computer names using the NetBIOS protocol, this structure is not valid.
Naming structure by DNS
The DNS naming structure uses a single server as a central server for naming systems and has a hierarchical and inheritance structure that allows large networks to be easily named without interfering with the naming of computers. . DNS is actually a server and the naming structure that names systems based on it is known as FQDN or Fully Qualified Domain Name and is basically designed for very large networks and the Internet. As we know the names of computers as NetBIOS Names in the NetBIOS protocol, we know them as host names in the DNS protocol, most of the time considering that a Host Name has the same number of characters as the NetBIOS Name, they are considered similar, if These two have completely different work structures. In DNS, there is no naming limitation that exists in NetBIOS naming, and for this reason, many computers can be named with this system.[1]
Introducing CVE-2016-3213 and CVE-2016-3236 exploits
Vulnerable platform: Windows that do not have the MS16-077 and MS16-063 security patches installed on their system.
Security patch release date: 6/14/2016
Vulnerability Type: Elevation of Privilege
An attacker who can successfully exploit these two vulnerabilities can gain access level elevation in the target system. To exploit this vulnerability, an attacker could respond to NetBIOS name requests for WPAD. The security patches provided address the vulnerability by correcting how Windows handles the proxy discovery process.
In this type of attack, the attacker does not need to be present in the LAN network. This vulnerability can be exploited by opening the browser (old versions) or opening an office document. In general, when using a URL link or unc path embedded in a file, it is possible to send a WPad request through the NBNS protocol.
Causes of this vulnerability:
- When the Windows operating system tries to resolve names such as “WPAD” and “FileServer”, it broadcasts the NBNS NB request in the network and the received response is accepted regardless of the sender’s IP address.
- When Windows tries to access a network address via IP, but the destination IP is unreachable (packets sent to port 139, 445 are timed out or the connection is reset), the NBNS NBSTAT request is sent to the destination address. will be
General suggested solutions
- Install the security patches provided by MS16-063 and MS16-077
- Closing port 137 for the UDP protocol in the firewall (this solution is not optimal)
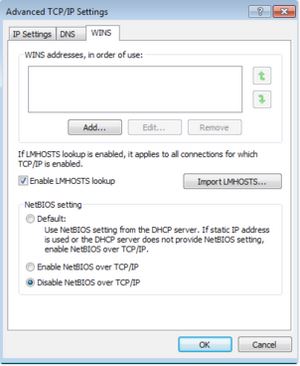
- For users who do not need Windows network sharing services, disable NetBIOS from the advanced tab of the network card: by clicking on the desired network card, the IPv4 section, from the general tab of the advanced option, by referring to the WINS tab, you can disable NetBIOS.
- Set an IP address for WPad in the route
%systemdrive%\Windows\System32\Drivers\etc\hosts
- with amount
255.255.255.255 wpad
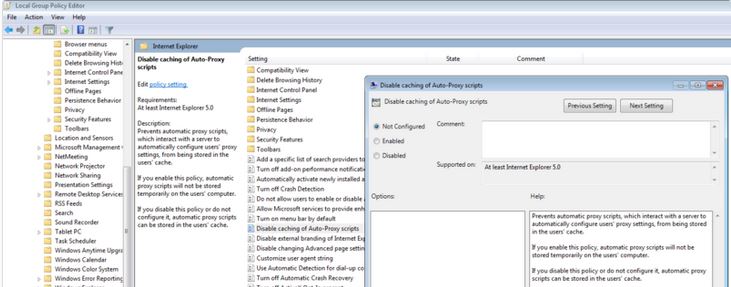
- Disable WPad via Group Policy Editor
through the run and entering the gpedit.msc command and referring to the path:
User Configuration\Administrative Templates\Windows Components\Internet Explorer
In the Disable caching of Auto-Proxy scripts section, you can enable it.
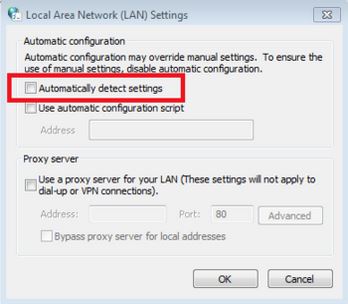
- Disabling automatic proxy discovery from the following path:
Internet options -> connection -> LAN settings -> automatically detect settings