Problem
- You see the following alert:
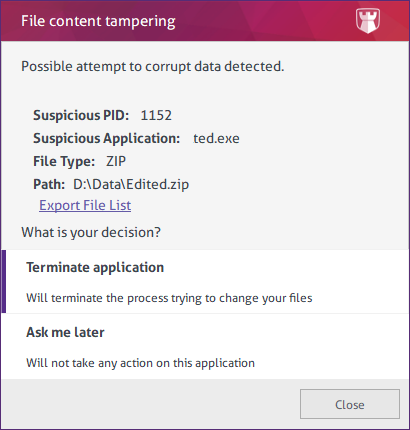
- Alert Message: Possible attempt to corrupt data detected. What is your decision? Terminate application / Ask me later.
- In the “Anticrypto” logs, you see a log with this field: Event = Tamper Attempt.
Root Cause
This message warns you about ransomware (very dangerous) or ransomware-like (clean, but similar in behavior to ransomware) activity.
So you should continue with extreme caution. Please read and apply carefully, or contact Padvish Support.
To understand the specific reason, you should note the “File Type” column.
There are 3 cases:
1) Bait: This means a program tried to change/delete/rename Padvish’s “bait” files. The files that Padvish places on the system to detect ransomware activity, and look like user documents. If an application tries to change these, we detect it as unusual activity.
2) SDA: This is a special kind of file deletion activity mainly seen in some ransomwares.
3) …: Anything different from above is the name of a file type (e.g. PNG, TIF, ZIP, …). This means some programs tried to overwrite a PNG/TIF/ZIP/… file with other content.
Case 1 (Bait)
This normally happens only when a user has enabled viewing hidden files and stomps on one of the bait files. When they try to delete the file or even double click to open it and see what’s inside, they’ll receive the alert. In this case, this is completely expected, and the user can be trained to not touch the files. (or disable viewing of hidden files)
But in no case should this happen on its own. No application should tamper with these files. If it happened without user involvement, it is most definitely malware.
Case 2 (SDA)
This is a special case. The application is trying to truncate the file before deleting it which is unusual. (If you’re deleting a file, why are you truncating it?)
Some ransomwares use this trick to make data recovery hard. So Padvish flags this behavior as suspicious.
Case 3 (File Type Change)
This case is highly popular with ransomwares and data wipers.
But it sometimes occurs with Web Applications, Document Scanners, or some other applications that use a temporary file to save or receive data, and then transfer it to its location.
For example, an scanner software that can store the scanned picture as TIF, JPG, and other formats. If the scanner “forgets” to delete the previously scanned document which was in the TIF format, and now decides to overwrite the file with JPG, it can cause this alert.
Similarly, a web application (usually running under w3wp.exe) that receives “attachments” and stores them in a temp file, can cause this alert if it forgets to delete the previous file and overwrites it with another file type.
Solution
So you should continue with extreme caution.
You can trust the application, but you need to be sure it is not malware.
You should check these parameters:
1 – Is the application a malware or a benign program? Is it infected or not?
2 – Is the file being overwritten, a file path that the application should be overwriting?
3 – Is this a one-time alert or is it recurring?
Please never trust these applications: svchost.exe, rundll32.exe, explorer.exe. Because these are frequently misused by malwares.
Here is guidance to answer these questions:
1 – Is the application a malware or not?
You cannot use antivirus scanners (the malware may be too new to be detected by any antivirus): So you should use your knowledge about the application.
Generally, it is not a malware if:
a) It has been on the system for some time (Check “Date Created” property on the application’s exe file and its parent folder),
b) It is in its usual path (i.e. It is installed as a regular program in an obvious place)
c) It is the app that the user knows about (If the user doesn’t know about it, it is suspicious)
d) It is the app you are using (You can link a Window to an application, using Task Manager. Just right-click the row showing info about the window and click “Go to details / Go to process”)
If ALL the questions are OK, then it is most possibly not a malware. (But please answer the other questions before decision)
If you’re unsure, DO NOT TAKE ANY RISKS. Please call Padvish Support and ask for help.
2 – Is the file related to the application?
Sometimes, a seemingly clean application (eg. Microsoft Word) is infected or otherwise tricked by malware to encrypt your files. So you should only allow an application to change a file if it is related to that file.
If you cannot find an obvious connection between the application and the file, again: DO NOT TAKE RISKS.
3 – Is this recurring?
If an application is repeatedly generating alerts, on its own, and on different files, this is HIGHLY SUSPICIOUS. Please don’t trust it in this situation and SEEK SUPPORT.
But if the alert is always occurring on a specific occasion (For example each time you click a button) and on a specific file, it is not so suspiciuos. And you can decide about it using the above questions.
How to create the exception
If you want to trust the application, you can do so in the Padvish Management Console:
- You can apply this setting to a group of computers: So either create a new group for computers that use this application or use an existing suitable group.
- Right Click on the group > Change Client Settings > Padvish AntiCrypto > Tamper Protection > Exceptions
- Click “Add By Application Path”, and enter the full application path. Select “Use In Tamper Protection”. (Please be careful which application you trust. You’ve been warned!)
Never ever trust svchost.exe, rundll32.exe, explorer.exe, and other executables which can load and act on behalf of malware.
That’ll fix it.
More things to do…
Finally, if the application causing alerts is yours or you have contact with the vendor, you can ask them to first delete the file, and then fill it with content. This way the application’s behavior will be different than that of ransomwares, and the antivirus will not alert about it.